Distributed Ledger Technology (DLT) has gained significant traction in recent years, with cryptocurrencies like Bitcoin and Ethereum becoming household names. DLT has the potential to revolutionize industries by offering increased transparency, security, and efficiency.
However, mass adoption of this technology is hindered by various challenges, with identity and proof of uniqueness being two of the most critical bottlenecks. In this post, we will delve into why these issues are central to mass DLT adoption and discuss possible solutions to overcome them.
The Importance of Identity in DLT
Identity and proof of uniqueness are fundamental to the functioning of any system that relies on trust and accountability. In the context of DLT, these concepts are essential for several reasons:
- Security: To prevent fraud, double-spending, and other malicious activities, it is crucial to ensure that each participant in a DLT system has a unique and verifiable identity.
- Accountability: In order to establish trust among users and maintain the integrity of a decentralized system, each participant must be held accountable for their actions. A strong identity framework is necessary for this.
- Compliance: Many industries and applications have regulatory requirements that necessitate the identification and verification of users. Implementing a robust identity management system is vital for DLT to be compliant with these regulations.
It is important for decentralized solutions to be compatible with the current worlds trust dynamics. Trust exists between an identity issuer and a verifier. A user receives an identity from an issuer, such as a government-issued ID, university diploma, or a domain certificate, and can present it to a verifier (e.g., a bank or employer) for validation.
The verifier trusts the ID issuer, not necessarily the user. In DLT systems, replicating this trust dynamic is essential to ensure a seamless and familiar user experience while maintaining the security and integrity of the system. By creating an environment that mirrors real-world trust relationships, DLT can foster user confidence and promote widespread adoption.
Challenges of Identity in DLT
Despite their importance, establishing identity and proof of uniqueness (PoU) in DLT systems has proven to be a complex challenge for several reasons. Before discussing these challenges, let’s first define PoU.
Proof of Uniqueness (PoU) refers to the process of verifying that a participant in a DLT system has a unique and non-duplicated identity. Ensuring PoU is essential for maintaining the security, integrity, and fairness of a decentralized system.
With this understanding, let’s consider the reasons why identity and PoU present challenges to mass adoption:
- Decentralization: One of the key advantages of DLT is decentralization, which removes the need for a central authority. However, this also makes it difficult to establish a unified, globally accepted identity management system and verify an actors uniqueness.
- Privacy Concerns: DLT systems often promise anonymity or pseudonymity, which can conflict with the need for identity verification and PoU. Striking the right balance between privacy and identity assurance is a challenge.
- Lack of Interoperability: Existing identity management systems are often siloed and lack interoperability. This can create friction when trying to establish a unified identity framework for DLT, as well as verifying PoU across different platforms.
To address these challenges, innovative solutions are being explored and developed, such as decentralized identity, zero-knowledge proofs, and interoperable identity frameworks.
Solutions
To address the challenges associated with identity and proof of uniqueness, several solutions are being explored:
- Decentralized Identity (DID): DID is a decentralized, user-centric identity management system that allows individuals to control their own digital identities. This approach has the potential to address the issues of centralization and interoperability.
- Zero-Knowledge Proofs (ZKPs): ZKPs enable identity verification without revealing sensitive information. This technology can help strike the right balance between privacy and identity assurance in DLT systems.
- Interoperable Identity Frameworks: Organizations like the Decentralized Identity Foundation (DIF) are working on creating interoperable identity standards that can be adopted across various DLT platforms, streamlining the identity verification process.
Here it is worth mentioning a solution that brings together the three aforementioned approaches to tackle the identity and proof of uniqueness bottlenecks in DLT – Polygon ID
Polygon ID
Polygon ID’s identity infrastructure promotes secure, trusted relationships between apps and users, adhering to self-sovereign identity principles and prioritizing privacy. It allows organizations to issue verifiable credentials about users and other organizations to verify these claims using a range of tools designed for the SSI ecosystem.
By combining these three powerful solutions, Polygon ID has the potential to significantly reduce the friction associated with identity and proof of uniqueness in DLT systems, paving the way for broader adoption of this transformative technology.
Polygon ID Architecture
Polygon ID’s framework architecture consists of three modules: Identity Holder, Issuer, and Verifier, together forming the Triangle of Trust. Each entity plays a crucial role in Polygon ID.
- Identity Holder: An entity possessing claims in their wallet. Issuers provide a Verifiable Credentials (VCs) to the holder, who then generates zero-knowledge proofs and presents them to the verifier for authentication against specific criteria.
- Issuer: An entity (person, organization, or thing) issuing VCs to holders, with each VC cryptographically signed by the issuer.
- Verifier: This entity verifies the holder’s proof, requesting proof based on the VCs in the holder’s wallet. The verifier performs checks, ensuring the VC is signed by the expected issuer and matches the requested criteria. For example, in a bar verifying age, an identity holder using Polygon ID would only need to provide a proof instead of revealing personal information. It worth noting that the verification of a VC can happen both off- and on-chain.
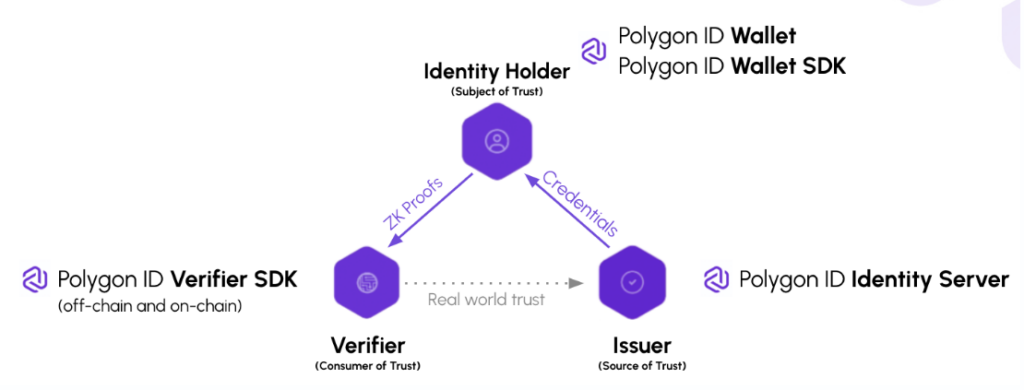
The Triangle of Trust of Polygon ID
What Can you Do With Polygon ID?
Leveraging zero-knowledge proofs, Polygon ID enables users to authenticate their identity without revealing private information, ensuring both freedom of expression and privacy by default.
- Privacy with Zero-Knowledge Proofs: Identity holders can protect their personal data using zero-knowledge proofs. During verification, they only need to prove ownership of a valid credential without revealing its content. For example, proving one’s age is over 18 without disclosing the exact age. This minimizes data exposure and prevents issuers from tracking credential usage.
- Off-Chain and On-Chain Verification: Proof verification can occur off-chain or on-chain via smart contracts. Developers can create contracts that distribute tokens to users meeting specific criteria based on their credentials.
- Self-Sovereignty: Polygon ID empowers users with self-sovereignty, allowing them to control their private keys and share data with third parties without issuer permission.
- Transitive Trust: This trust model enables easy trust extension across domains or contexts. Information from one issuer can be used by multiple verifiers without permission, and identity holders can build trust by accumulating credentials from various issuers in a single digital wallet.
Closing Remarks
Identity and proof of uniqueness are central to the successful mass adoption of DLT. By addressing these bottlenecks and implementing robust, decentralized, and privacy-preserving identity management solutions, DLT can unlock its full potential and evolve industries across the globe. As the technology continues to mature, overcoming these challenges will be essential to shaping a more transparent, secure, and efficient digital world.
Sources
Polygon ID (Polygon)
Zero Knowledge Proofs (Ethereum org)
Verifiable Credentials (w3 org)
Decentralized Identifier (w3 org)
Join those who stretch the possible.
Weekly exclusive email to help navigate DeFi and crypto. No trivial stuff, no news aggregation. We dive deep into the world of DeFi and pull together resources that we find useful on the road toward financial freedom.
We value your privacy and time. We will never share your information nor send irrelevant 
Hello, new money!
Redcurry is a truly independent digital currency backed by commercial real estate.